Verifiable Credentials
An open standard for digital credentials that securely represent verifiable information.
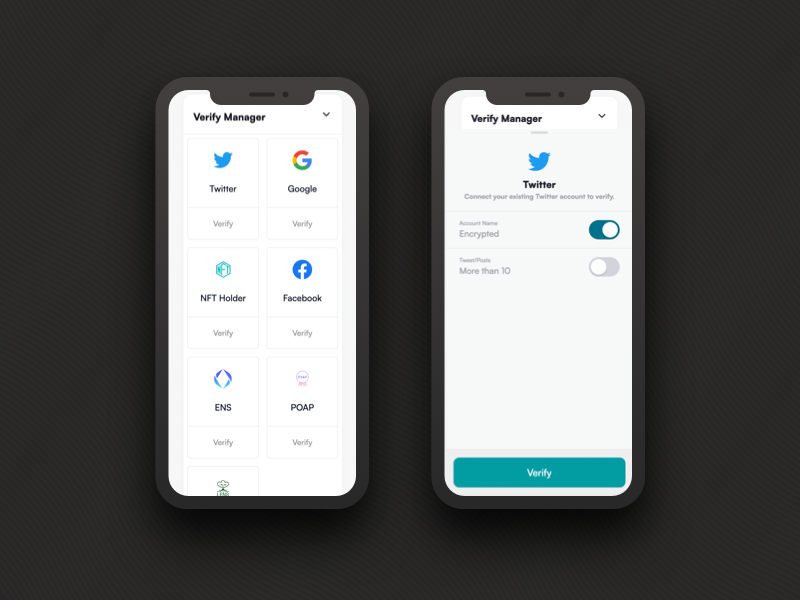
Configure an IP domain with any information you would like to be cryptographically verified and linked to your registered domains.
The vast applications of Verified Credentials (VC.iD) range anywhere from securely verifying official social media accounts to activating access control keys, cards, fobs, badges and even fully customizable and scalable tracked achievements for specific tasks and communities. A great example of a core implementation of this is a POAP (Proof of Attendance Protocol) which can be automatically issued based on completely customizable and programmable criteria.
Scalable, composable and secure blockchain infrastructure can now be implemented in the most practical and accessible user context. VC.iD represents a new paradigm of user sovereignty and custody.

EBPTO developed the VC.iD to configure domain specific verifiable credentials. The system employs a hybrid architecture with both on-chain and off-chain components for maximum efficiency and flexibility.
Each domain is issued a VC.iD scope containing a cryptographically signed message. These signed messages are tamper-proof and self-authenticating. This concept is very similar to a traditional passport—additional credentials are saved in these passports just like stamps are as recorded proofs.
The VC.iD scope is saved on Ethereum through the EBPTO domain registry. Additional signature data is replicated on Gnosis Chain (xDAI) and IPFS for cost optimization.
The credentials can remain pseudonymous. Individual users can operate multiple domains simultaneously. For example: a real-name personal domain as well as a company domain.
Why Verifiable Credentials?
Today, most domain products solely focus on resolving complex addresses to readable names using a DNS like interface allowing people to enter anything they like into plain text input fields.
While this free field method is flexible, it does not at all prevent misinformation or impersonation. (e.g. Using the free field model, one could easily enter "ElonMusk" into a Twitter record or "Vitalik" into a Mastodon record).
EBPTO's Verifiable Credentials employ a bi-directional signed proof, containing and requiring additional information from a valid authenticated session from the issuer side (Twitter, Google, etc). This more robust system is becomes exponentially more secure vs. the now dated uni-directional models used by other domain protocols.